Network Address Translation (NAT) is a technology that has, in a small way, revolutionized Internet communications. NAT allows multiple computers on a LAN to share a single public IP address for accessing the Internet. NAT also hide private hosts; causing peers not reachable globally. In NATed environment, general firewall/NAT gateway does not allow incoming connection to private addressed hosts. This makes it hard to locate and communicate with the private hosts behind a NAT gateway. For example, a web browser in the hidden/masqueraded network can browse a website outside, but a web browser outside could not browse a web site in the hidden/masqueraded network.
IP video based solutions provide an easy way to capture and distribute high-quality video over any kind of IP network or the Internet. The video can be stored at remote locations for convenience and security, and the information can be transported or viewed over the LAN or Internet.
The Challenge
Network Address Translation (NAT) causes well-known difficulties for peer-to-peer (P2P) communication, since the peers involved may not be reachable at any globally valid IP address. Setting up a remote access to video surveillance is a challenge; with companies having firewalls and other hardware and software security measures in place; to safeguard against security breaches.
NAT Traversal
Video management solutions intending to provide anytime, anywhere remote video access need to establish a peer-to-peer network between the server and the host, Peer-to-peer network is different as compared to a client-server network. In a peer-to-peer network, peers have equal positions without classification of client and server. They act both as client and server simultaneously.
In a peer-to-peer network, hosts behind NAT gateway can be reached directly by the server and a communication tunnel is established between the two. This mode of communication is called as NAT Traversal. NAT Traversal technique enables end-to-end protocol and application packets through NAT gateway directly or indirectly.
NAT traversal techniques are typically required for client-to-client networking applications, especially peer-to-peer and Voice-over-IP (VoIP) deployments. There are various NAT Traversal techniques that offer diverse, transparent traversal abilities to keep the virtual end-to-end connection enabled. Some methods use the server only when establishing the connection (such as STUN), while others are based on relaying all data through it (such as TURN), which adds bandwidth costs and increases latency, detrimental to real-time voice and video communications. Some of these techniques are:
- Universal Plug and Play (UPnP)
- Application Level Gateway (ALG)
- TCP/UDP hole punching
- Simple Traversal UDP Through NAT (STUN)
- Traversal Using Relay NAT (TURN)
Universal Plug and Play (UPnP)
UPnP is an open standard architecture for flexible connectivity of both wired and wireless devices. In home/SOHO settings, Universal Plug and Play (UPnP) is supported by most small NAT gateways.
Application Level Gateway (ALG)
ALG allows customized NAT traversal filters to be plugged into the gateway to support address and port translation for certain application layer “control/data” protocols. In order for these protocols to work through NAT or a firewall, either the application has to know about an address/port number combination that allows incoming packets, or the NAT has to monitor the control traffic and open up port mappings dynamically as required. Legitimate application data can thus be passed through the security checks of the firewall or NAT that would have otherwise restricted the traffic for not meeting its limited filter criteria.
TU Hole Punching
TCP and UDP (TU) hole punching is the most robust and practical NAT traversal technique. This technique does not require the application to know the topology of network and presence of NAT devices. It does not modify NAT/Firewall configuration. It makes use of a rendezvous server as an introducer for clients behind NAT to get know each other’s host endpoints (IP address and TU port). Unfortunately, TU hole-punching does not work with symmetric NAT.
Simple Traversal UDP through NAT (STUN)
STUN is lightweight simple client-server model protocol to allow the applications in private address realm to discover the presence of NAT devices and the type of NAT between them and public address realm. STUN clients can learn address and port binding used on NATs by sending and receiving exploratory request and response messages.The advantage of STUN is it does not require any changes on NAT devices. Clients can learn NAT devices automatically. On the other side, STUN does not work with symmetric NAT which is commonly used by large corporate users.
Traversal Using Relay NAT (TURN)
TURN allows devices behind a NAT to receive incoming data over TCP or UDP. It is most useful for symmetric NATs or firewalls that wish to be on the receiving end of a connection to a single peer. TURN does not allow for users to run servers on well known ports if they are behind a NAT; it supports the connection of a user behind a NAT to only a single peer.
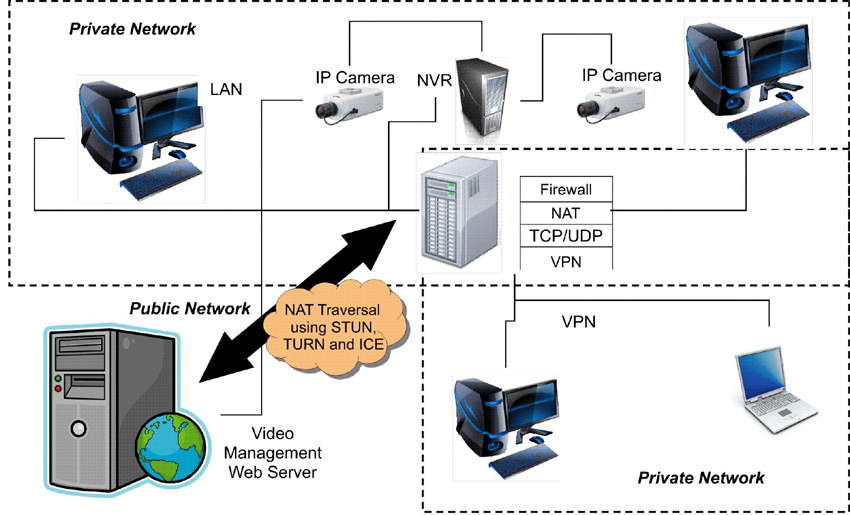
The Ideal Solution
Each of these methods have a limitation, and to address and resolve this; the IETF (Internet Engineering Task Force) has devised a suite of protocols, namely STUN, TURN and ICE, which in combination address the limitations of the various available NAT traversal methods listed above. STUN lets the applications discover the public IP address and port mappings that the applications can use to communicate with its peer. TURN, on the other hand, allocates a public IP/port on a globally reachable server and uses it to relay media between communicating parties. ICE is a framework that defines how to use the STUN and TURN protocols to solve the NAT traversal problem, by choosing the best possible interconnection method between two users.
Conclusion
This IETF STUN, TURN and ICE NAT traversal technique provides smooth and secure communication to establish a peer-to-peer network NATed environments; that helps provide seamless access to real-time IP video anytime, anywhere in the world through the internet.



