[Note: This article used inputs from the following site’s – http://www.arstechnica.com – section: Law & Disorder]
Introduction
One of the Homeland Security May 2011 Tech. Briefs – Using Social Networking Sites and Tools for Intelligence-gathering – briefly discussed the opportunity for intelligence-gathering, by government and private agencies, provided by social networking sites. A recently concluded operation by the FBI (USA) saw the unmasking of the leading hacktivists belonging to an off-shoot of the Anonymous hacktivist movement, and has lessons for law-enforcement agencies in India.
This brief lays out the chronolgy of events leading to the identification and arrests of the members of the off-shoot.
Who or What is Anonymous?
Anonymous is an Internet activist movement that espouses causes mainly related to on-line piracy (or the opposition to it), regulation of the Internet, freedom of speech, and intrusive government (not necessarily non-democratic governments only). Its preferred mode of operation, in espousing such causes, is through hacktivism: “the non-violent use of legal and/or illegal digital tools in pursuit of political ends”.
The point to note about Anonymous is that it is an amorphous, non-hierarchical community, with no membership norms or procedures, no fixed chain-of-command structures, and no single spokesperson. Although it first rose to prominence in its on-line attacks on organisations and individuals opposed to on-line piracy, it has since made a name for itself in its hacktivist activities against entities and governments seen muzzling free speech and dissent, as well as against “parasitic” commercial organisations.
 |
 |
| Figure 1: On-line (left) and real-life (right) signifiers for Anonymous Credit: Wikipedia |
|
When a cause has been identified, the individual tries to rally other potential hacktivists, and if there is sufficient sympathy and commitment to the cause, an informal group (an off-shoot) forms and plans one or several hacktivist activities aimed at providing publicity to the cause or at disrupting the operations of organisations identified as opposing the cause.
Anonymous hacktivists typically co-ordinate activities through IRC (Internet Relay Chat) channels, imageboards, social networking sites, and other such portals where anonymity is ensured. In addition, hacktivists use private VPNs and Tor – a tool and system that ensures on-line anonymity – when logging on to the Internet, to ensure that activities on the Web cannot be traced back to a specific IP address.
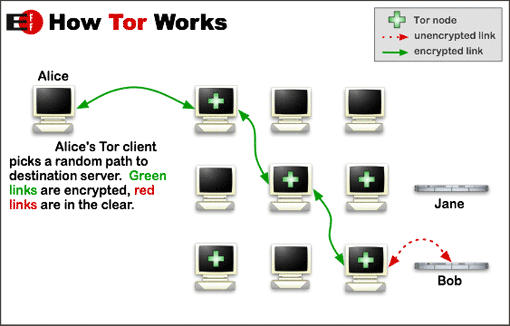 |
| How Tor Works: After obtaining a list of Tor nodes from a directory server, Alice’s Tor client picks a random path to destination server Bob. Credit: Wikipedia |
Timeline of Events Leading to the Unmasking of LulzSec and AntiSec
The events leading to the unmasking of a group of Anonymous hacktivists can be traced to the United States diplomatic cables leaks by Wikileaks, back in 2010, and the timeline below explains the major incidents leading up to the denouement.
Lessons to be Learnt
The unmasking of the participants of the LulzSec and AntiSec campaigns has some important lessons for homeland security intelligence officials in India.
- There is no true anonymity on the Internet
With the exponential growth of social networking sites and other content aggregators, it is becoming clear that there is no true anonymity on the Internet. Any individual planning an illegal on-line operation has potentially disclosed something personal in one or many of such social networking sites or in chat groups: information that can be leveraged by law-enforcement agencies to identify the individual. Social Network Analysis (SNA) tools can form relationships between profiles set up in different sites, between multiple personae created by the same individual, and cross link them to other information on the Internet, to get a handle on the identity of the offending individual. - On-line intelligence-gathering has to go hand-in-hand with traditional intelligence-gathering
In the above case-study, the FBI complemented its on-line intelligence-gathering activities with traditional intelligence-gathering activities. In the case of one of the hackers, he let slip a piece of information regarding having attended a protest march a few months prior, and the FBI was able to access video surveillance footage of the march; thereby allowing it to identify individuals at the protest march with existing criminal records, and then build up a list of suspects. Once a suspect list was built, the individuals’ logging on/off was monitored on-line, and communicated to a separate team carrying out traditional SIGINT surveillance, to narrow down the list to the actual culprit. There was an element of luck in the investigation – slip-ups by the culprits – but that is par for the course in any investigation. - Movements such as Anonymous are extremely resilient
The last two rows of the timeline above mentions that Anonymous and, perhaps, LulzSec are planning new operations come the 31st of March and the 1st of April, respectively. The point to note is that on account of the structure of movements such as Anonymous (decentralized, non-hierarchical), they are extremely resilient; like the Lernaean Hydra of Ancient Greek mythology. If the core participants of one off-shoot are arrested, another set of participants will step in to fill the breach. Unceasing vigilance is the key to keeping the activities of such movements under check, because with every success of law-enforcement agencies, the targets get smarter: either in terms of using better tools or in terms of communicating only when necessary.
Conclusion
The above case-study points to a high-level methodology for tracking and identifying suspects accused of illegal on-line activities, whether these activities be targeted against a government or against a country’s critical infrastructure: provided the accused are private citizens, and not foreign-government agents operating from outside the country.
The Provisional IRA (Irish Republican Army) famously issued the statement, after the 12 October 1984 Brighton, England, hotel bombing (in which it targeted then UK Prime Minister, Margaret Thatcher): “…Today we were unlucky, but remember we only have to be lucky once. You will have to be lucky always. …” Given the hunter-hunted nature of this engagement, the same will be the view of law-enforcement agencies when targeting hacktivist movements.



