Introduction
One of the Tech. Briefs last month (November 2011) – The Sensor Cloud and Homeland Security – briefly outlined how Homeland Security agencies can use cloud computing to store and process surveillance sensor data. Although the focus in that brief was on traditional surveillance sensors – video, audio, radar, trace detectors, access control, motion detectors, etc. – the current implementations of sensor clouds all involve Wireless Sensor Networks (WSN) in areas as diverse as industrial process monitoring, environmental protection and management, structural monitoring of critical equipment and edifices, and consumer energy consumption management. With the proliferation of sensors on consumer devices, specifically smartphones, there exists an opportunity to leverage the availability of such sensors, at a relatively lower cost than specialized sensor-carrying devices or custom-built sensors, to build a WSN targeted at unearthing and identifying Homeland Security threats. This brief looks at the viability of deploying such WSNs.
Wireless Sensor Network (WSN)
A Wireless Sensor Network (WSN) is a set of spatially located smart-sensors, to measure one or more parameters ranging from temperature and pressure to capturing video or audio, that feed their data over a common backbone to a repository for storage and analaysis. The smart in smart-sensors refers to the ability of the sensor to transmit data (either collected or requested by its control) through the available network, without any intervention from its control. The common backbone, or network, can be anything from a cellular network to a low-power short-distance network such as Zigbee.
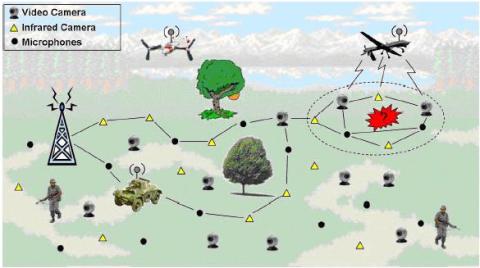 |
| Figure 1: Wireless Sensor Network for reconnaissance Credit: www2.ece.ohio-state.edu |
The components of a WSN are the nodes, that capture data on the parameter they have been designed to measure or detect; gateway nodes, that serve to transmit the data collected by a set of nodes to a central repository, as well as receive control data from the repository; and the repository, that stores and analyses the collected data, as well as administers the nodes and gateways. It is not always necessary that there is only one designated gateway node, to transmit and receive data, for a set of nodes: depending on the network architecture and the capacity of the network, every node may function as a gateway node.
While, so far, single-measurand sensors have been deployed in WSNs, for activities ranging from environmental monitoring to equipment monitoring; there is no reason a WSN cannot be built using a multi-sensor hosting device as the node. Given that the most popular multi-sensor hosting device in the world is the smartphone, it goes without saying that there are several efforts underway, worldwide, to exploit the sensorial capabilities of smartphones to capture and send data on different types of measurands.
A Smartphone WSN for Homeland Security
Today’s smartphone carries a range of sensors embedded in the deivce, and also offers options for attaching specialised sensors over Bluetooth or USB. Although intended for specific functions – for example the proximity sensor was incorporated in smartphones to sense whether the phone was being held to the ear, and if so, to reduce screen brightness and therefore conserve battery capacity – they have now been exploited for functions far removed from their original functional requirement – proximity sensors are now used to sense whether there is a person close to the possessor of the smartphone.
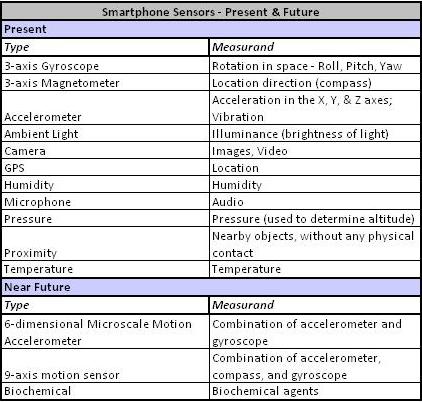 |
| Figure 2: Common Smartphone Sensors in existing devices, and new sensors expected shortly |
The potential to use these sensors for applications outside their intended is only limited by a user’s imagination. There are already thousands of applications available under the Android, Apple, and Windows Phone, that use these sensors for novel and very useful purposes.
Coming specifically to Homeland Security applications, the US Department of Homeland Security, through its Science & Technology Directorate (S&T) is carrying out a proof-of-concept of an initiative named Cell-All – crowdsourcing cellphones to detect dangerous chemicals. Working with a few smartphone manufacturers, S&T is carrying out trials of the use of chemical sensors in smartphones. These sensors will have the ability to detect the presence of gases such as ammonia, chlorine, CO (carbon monoxide), and methane; as well as of smoke. Based on the chemical detected, the smartphone will alert its possessor of the presence of a hazardous chemical, or call an Emergency Operations Centre (EOC) with details of time, location, and chemical. The crowdsourcing advantage comes to the fore when several such calls come pouring into an EOC, allowing Disaster Response teams to determine the extent of the crisis, work out possible causes, and then arrive at the scene prepared to deal with the crisis more effectively. Cell-All is currently under trial and it will be a couple of years before stock smartphones come equipped with biochemical sensors; but, the potential for leveraging the smartphone, for homeland security duty, is now there for all to see.
The Way Forward
Homeland Security agencies in India need to work on the lines of the US DHS and fund the CSIR Labs as well as the DRDO Labs to define and trial initiatives that leverage built-in and specialised sensors in smartphones to assist in homeland security tasks.
Use-cases:
A co-ordinating agency can define use-cases for potential deployment of smartphone sensors in homeland security functions. For example, one project may involve using smartphones to set up a quick and simple perimeter protection system for paramilitary patrol units in insurgency-affected territory, using the proximity sensors on the smartphones. Another may involve equipping all police personnel in localities identified as being high-risk, for terror strikes, chemical sensor enabled smartphones which can detect traces of explosives.
Applications:
In parallel with the development of specialised hardware should be the development of the application that will run on the smartphone, that will allow the hardware to be used for these specialised needs. Depending on the smartphones used or deployed, the applications will need to be written for Android, iOS, and Windows Phone.
Cautions
Although creating such a Homeland Security India Sensor Cloud will be a complex undertaking, a start can be made by setting up a basic infrastructure and connecting existing Web-connected sensor networks on an experimental basis, with willing agencies. However, before doing so, the following issues will need to be addressed:
- Security
Smartphones are already the target of hackers, and it is mandatory that security on the device is of the highest order, and follows a defined process, before any new application is deployed on the field. This may require the co-ordinating agency to develop device-specific hardware and software add-ons to ensure the required level of security. - Confidentiality and Privacy of Data
Since the data comes from various geographies and covers various physical parameters, the repository has to be designed such that sensor data, sensors, and associated information are not directly associated in the database. In addition, if there is going to be a crowdsourcing initiative similar to Cell-All, the identity of the providers of the data needs to be protected. Finally, there needs to be a policy for the duration of time data is retained and for the destruction of data outside this retention period. - Data Management
In any system involving hundreds and thousands of devices sending streams of data, the management of the data is crucial, to ensure that the right information is extracted from the streams in the right time. In addition, decisions such as whether to leave a copy of the data at the originating device, whether to make the data available to the possessor of the device, etc. need to be taken and enforced. - Transmission Network Redundancy
Mobile networks are typically the first to crash during a crisis, on acount of the surge in traffic. Given this knowledge, any system that leverages smartphones will need to decide up front that once a crisis kicks in all data transfers will cease; or, alternatively, make provisions for network redundancy (say, through a mix of wired and wireless backhauls).
Conclusion
This brief takes forward the idea enunciated in last month’s brief regarding leveraging technology for the protection of the homeland. The use of everyday technology reduces the cost of implementing new systems, while bringing in risks associated with the security of such non-hardened devices.
There is an enormous potential in the idea of leveraging smartphone sensors for homeland security functions, and the sooner authorities in India investigate this, the more effective is going to be homeland security apparatus in the nation.



