Introduction
There have been two attacks on Certification Authorities this year, so far. In both cases, the respective attacker successfully managed to issue bogus certificates to itself. The bogus certificates were issued in the names of Google, Yahoo, and Skype, among others.
The bogus certificates allowed a malafide operator to misrepresent itself as the above sites, and then have unsuspecting users access them; in the process stealing login/password information, and gaining access to private communications.
While, traditionally, such activities came under the purview of IT security experts, as they, more often than not, were executed with the intention of illicit commercial gain; more recently, the fact that many of such attacks are perpetrated by governments and state agencies, has implications for a nation’s security. This brief looks at the nature of the problem, its impact on homeland security, and ways of safeguarding a nation’s digitally-recorded and communicated information from its enemies.
Why is it that what a CA does is important?
A CA is a third-party who issues certificates establishing the identity of the entity in whose name the certificate has been issued. The reason that the function performed by the CA is important, is because encryption on the Web is performed using Asymmetric Cryptography; otherwise known as Public-Key Cryptography.
Public-Key Cryptography
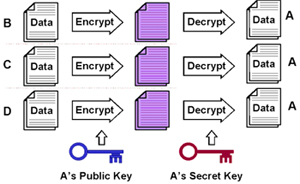
In Public-Key Cryptography, data communicated between two parties (the public and the owner) is encrypted using a combination of a public-key and a secret-key. The public-key is made available to the public, by the owner, while the secret-key is known only to the owner.
 |
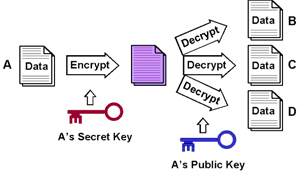 |
| Figure 1: Public-Key Cryptography (Credit: Eric Wilde, UC Berkeley School of Information – http://dret.net/lectures/web-fall08/security) |
Issuance of Certificates
The CA is the trusted party who verifies that the “owner” is whoever it says it is: whether a bank or a credit-card company or an on-line merchant. A certificate is a digital signature issued by a trusted party (the CA) confirming the identity of the entity, as well as the public-key for that entity. Browsers come pre-installed (by the browser vendor) with a list of trusted parties (root certificates); so, they do not accept certificates from any party.
Therefore, when an on-line entity passes on a certificate from a trusted party, the browser assumes that the entity is who it says it is, and will present the entity’s website to the user.
Fraudulent Issuance of Certificates
The problems arise when hackers infiltrate the CA, and have legitimate certificates issued. These certificates allow the hackers to present themselves to the public (through suitably designed webpages) as the organizations in whose names the certificates have been issued.
This is what happened to two CAs (Comodo, the third-largest CA in the world, and Diginotar, a Dutch CA). In the case of Comodo, a compromised partner account led to nine SSL certificates being issued to the hacker. In the case of Diginotar, it is not clear how the hacker gained access to the certificates. The hacker’s IP address, in the case of the Comodo attack, was traced back to Iran. The same hacker has claimed responsibility for the Diginotar attack.
Implications of Bogus Certificates
When state agencies get into the business of hacking CAs, the reason is rarely pecuniary; it is for reasons of on-line monitoring or intelligence-gathering. There are three major for users, from the issuance and usage of bogus certificates:
Harvesting login IDs and passwords
Using a bogus certificate, a hacker can set up a fake website/webpage that fools users into entering confidential information. This information may be used to access private on-line accounts of the user: e-mail accounts, banking transactions, etc.
 Man-In-The-Middle attack
Man-In-The-Middle attack
A Man-In-The-Middle (MITM) attack is an operation where an unauthorised entity inserts itself in a communication between two parties. The attacker may merely eavesdrop on the communication, or may even modify the communication; without the two parties being aware of it. For example, surveillance video streams from surveillance cameras at a critical infrastructure facility may end up being intercepted, en-route from a local video recorder to remote viewers, and doctored to ensure that intrusions are not spotted.
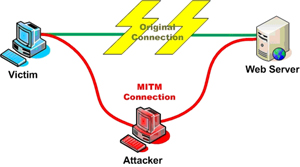 |
| Figure 2: Illustration of Man-In-The-Middle Attack (Credit: The Open Web Application Security Project, owasp.org) |
Inserting malware in a User’s PC
The most sophisticated hackers use a combination of bogus certificates and DNS hacking to insert malware in a user’s PC. Such software will then allow the hacker complete access to the contents of the PC or allow the hacker to use the PC for other illegal activities. An earlier brief, from April 2011 – Rootkits, Kill-Switches, and Backdoors_Implications for Homeland Security – covers the various methods used by hackers to gain control of an on-line computing resource.
If Trusted Parties cannot be trusted?
- It is very difficult for a user to identify an instance of a bogus certificate being presented to a browser. Typically, such incidents are unearthed by IT security experts poring over anomalies in the routing of communications in the Internet. However, as a user, there are a few precautions that can be taken when surfing the Web:
- Keep an eye out for warnings on-line about CAs being hacked for certificates, or for news about fraudulent issuance of certificates
- Ensure that these certificates are revoked by the web browser
- Browser-related
- Ensure that the browser version is the latest
- Enable certificate revocation in the browser security settings
- Customise root certificates in the browser’s list
- Always look for the “green bar” in the browser’s address bar, when entering confidential information or when signing on to a site where data is going to be stored or uploaded. The green bar indicates that the website has gone through an Extended Validation (EV) process, and has been certified to be what it claims to be.
Conclusion
The increasing volume of data on the Internet and the ubiquity of on-line communications has increased the risks of confidential data and private communications falling into the wrong hands. With state agencies now getting into the hacking business, for reasons of surveillance or espionage, it is important for Homeland Security agencies to monitor the virtual world as intensively as they do the real world.



